Purpose Limitation Compliance with OpenAI | Cyera Blog
Security Boulevard
JUNE 20, 2023
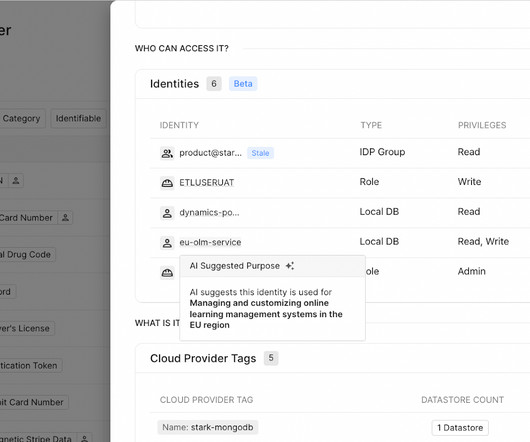
Background on Purpose Limitation Purpose limitation is the principle that PII collected for a given purpose may not be used for a different purpose. According to GDPR Article(5) (1)(b), further processing of PII may be permitted when the reason is not “incompatible with the initial purposes” and for “archiving purposes in the public interest.”















































Let's personalize your content