Malicious Download Links Impersonating Popular Software Pushed by Hackers Through Google Ads
Heimadal Security
JANUARY 18, 2023
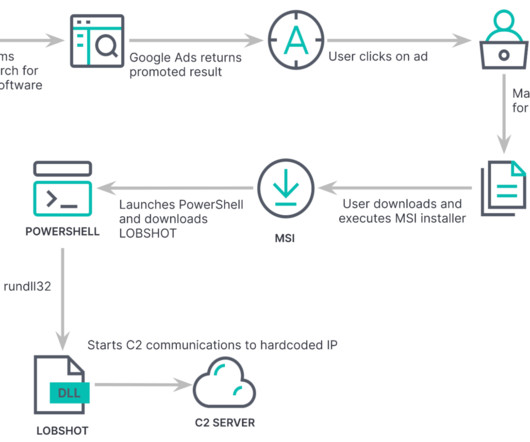
Security researchers discovered that lately a lot of fake websites impersonating popular free and open-source software have started to pop up in the sponsored section on Google search results. Crypto Influencer Stripped of NFTs At least one well-known cryptocurrency user claims to have been […].






































Let's personalize your content