Weekly Update 352
Troy Hunt
JUNE 17, 2023
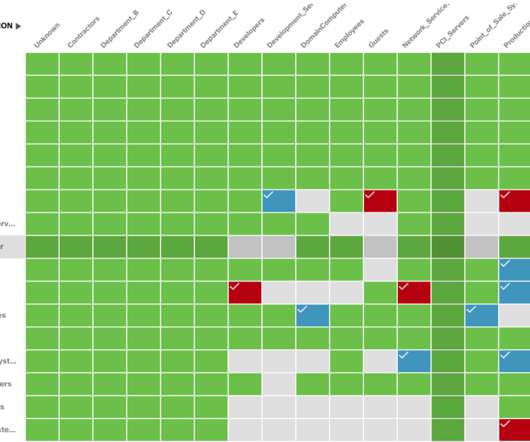
Domain searches in HIBP - that's the story this week - and I'm grateful for all the feedback I've received. I need to keep writing code, revising the draft blog post to announce it then sometime in hopefully about a month, push it all live. It's Zero Trust for Okta. Want to see for yourself?










































Let's personalize your content