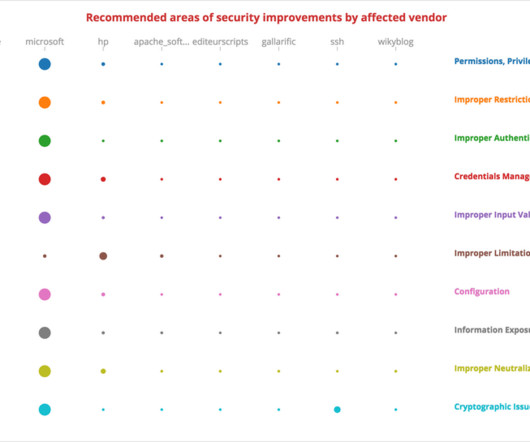
Best Practice Steps for Safe Data Sharing
Security Boulevard
MAY 24, 2021
<a href='/blog?tag=Data tag=Data Security'>Data Security</a> <a href='/blog?tag=Data tag=Data Breach'>Data Breach</a> <a href='/blog?tag=Information study by IBM, the average cost of a data breach is now estimated at $3.92 According to a?study Download the Guide.





















Let's personalize your content