GUEST ESSAY: JPMorgan’s $200 million in fines stems from all-too-common compliance failures
The Last Watchdog
JANUARY 13, 2022
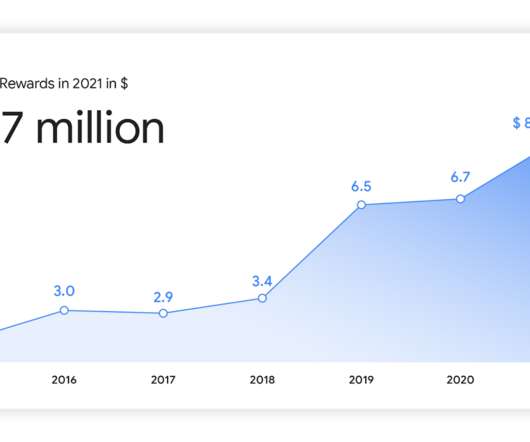
While the price tag of these violations was shocking, the compliance failure was not. The ever-changing landscape of rapid communication via instant messaging apps, such as WhatsApp, Signal, WeChat, Telegram, and others, has left regulated industries to find a balance between compliance and efficient client communication.






















Let's personalize your content