GUEST ESSAY: Why online supply chains remain at risk — and what companies can do about it
The Last Watchdog
JUNE 30, 2021
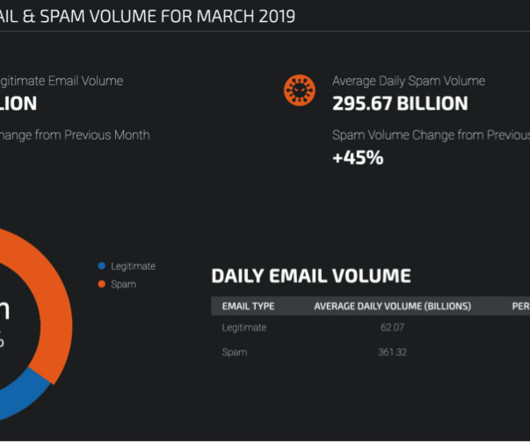
Enterprises have long operated in an implicit trust model with their partners. This simply means that they trust, but don’t often verify, that their partners are reputable and stay compliant over time. are used to gain access to third party servers. So what does the average modern website look like?


























Let's personalize your content