These are the 15 Top Cyber Threats Now
SecureWorld News
NOVEMBER 12, 2020
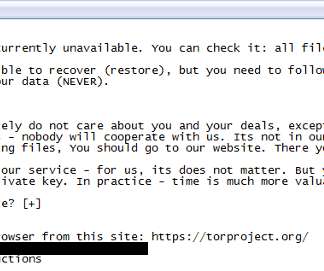
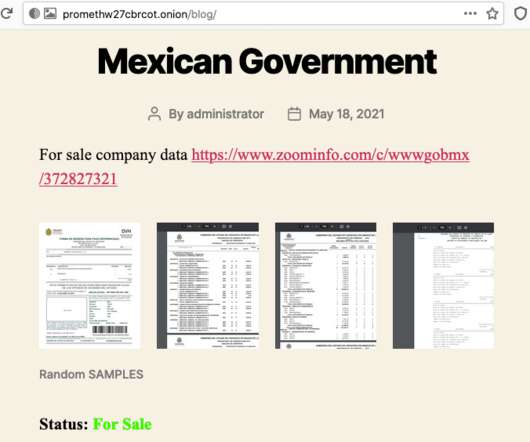
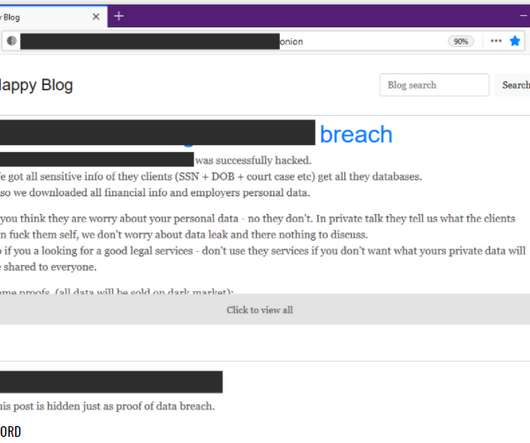
Sometimes when you are down in the cyber attack trees defending your organization, it can be tough to see the cyber threat forest. Understanding how things are shifting in the forest, or overall threat landscape, can help us categorize, strategize, and prioritize our resources. What are the top cyber threats right now?















































Let's personalize your content