Bomb Threat, DDoS Purveyor Gets Eight Years
Krebs on Security
DECEMBER 1, 2020
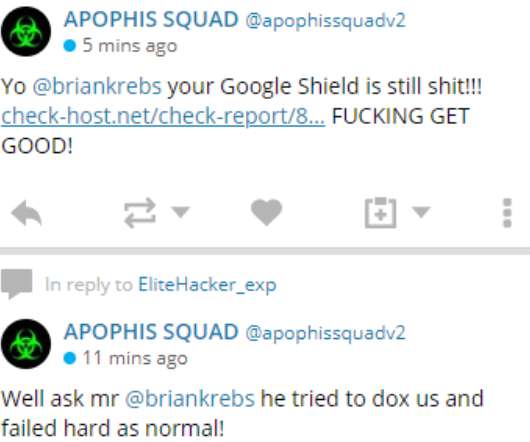
and United Kingdom, running a service that launched distributed denial-of-service (DDoS) attacks, and for possessing sexually explicit images of minors. The Justice Department says Vaughn and his gang ran a DDoS-for-hire service that they used to shake down victims. The DDoS-for-hire service run by Apophis Squad listed their members.













































Let's personalize your content