NSA, CISA issue guidance on Protective DNS services
SC Magazine
MARCH 4, 2021
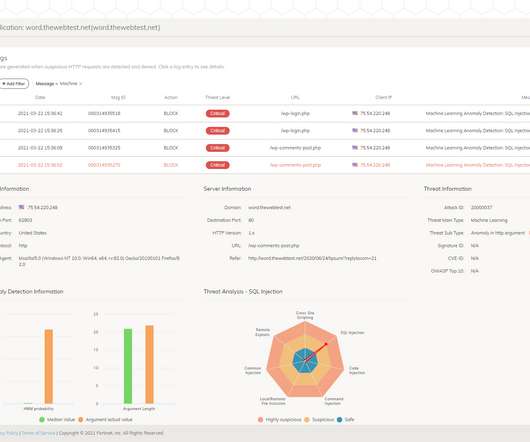
A PDNS service uses existing DNS protocols and architecture to analyze DNS queries and mitigate threats. A PDNS can log and save suspicious queries and provide a blocked response, delaying or preventing malicious actions – such as ransomware locking victim files – while letting organizations investigate using those logged DNS queries.














































Let's personalize your content