Why Governments Worldwide Recommend Protective DNS
Security Boulevard
AUGUST 7, 2024
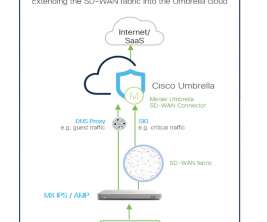
HYAS Protect protective DNS uses advanced data analytics to proactively block cyber threats, a feature unavailable in legacy systems relying on static DNS filtering. AV-TEST , one of the cybersecurity industry’s most trusted evaluators, rates HYAS as the most effective protective DNS solution on the market.












































Let's personalize your content