Weekly Update 366
Troy Hunt
SEPTEMBER 22, 2023
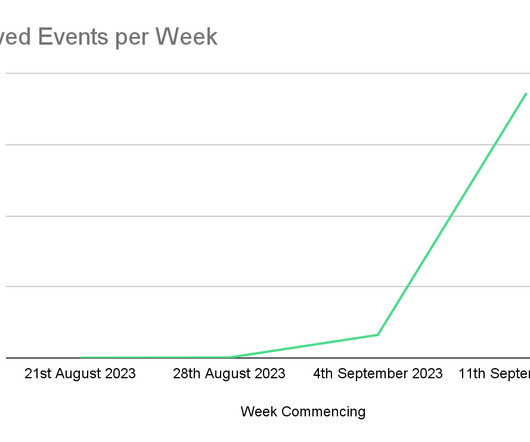
Well that's it, Europe is done! I've spent the week in Prague with highlights including catching up with Josef Prusa, keynoting at Experts Live EU and taking a "beer spa" complete with our own endless supply of tap beer. Life is good 🍻 That’s it - we’ve peaked - life is all downhill from here 🤣 🍻 #BeerSpa pic.twitter.com/ezCpUC6XEK — Troy Hunt (@troyhunt) September 21, 2023 All that and more in this week's video, next week I&apo




































Let's personalize your content