Spaf on the Morris Worm
Schneier on Security
NOVEMBER 7, 2023
Gene Spafford wrote an essay reflecting on the Morris Worm of 1988—35 years ago. His lessons from then are still applicable today.

Schneier on Security
NOVEMBER 7, 2023
Gene Spafford wrote an essay reflecting on the Morris Worm of 1988—35 years ago. His lessons from then are still applicable today.

The Last Watchdog
NOVEMBER 7, 2023
Throughout 2023, we’ve witnessed numerous significant cyber incidents. One of the largest this year was the MOVEit breach, which impacted various state motor vehicle organizations and exposed driver’s license information for nearly 9.5 million individuals. Related: The Golden Age of cyber espionage We have also seen ransomware outbreaks at MGM and Caesar’s Casino , causing losses in the millions of dollars and targeted assaults on the healthcare sector, affecting over 11 millio
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
NOVEMBER 7, 2023
The Australian government is moving towards regulating cryptocurrency, with a focus on those involved in developing and maintaining crypto platforms.

Bleeping Computer
NOVEMBER 7, 2023
Microsoft has introduced a new protective feature in the Authenticator app to block notifications that appear suspicious based on specific checks performed during the account login stage. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

The Last Watchdog
NOVEMBER 7, 2023
Boston, Mass., Nov. 7, 2023 — AppMap today announces its innovative Runtime Code Review solution that will transform software quality and the developer experience. AppMap’s mission is to deliver actionable insights to developers where they work, and AppMap continues to deliver on the promise with its latest release for the GitHub Marketplace. Unexpected runtime defects account for a staggering 40% of performance problems and 50% of security defects.

WIRED Threat Level
NOVEMBER 7, 2023
The Government Surveillance Reform Act of 2023 pulls from past privacy bills to overhaul how police and the feds access Americans’ data and communications.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
NOVEMBER 7, 2023
Okta has revealed details about a recent breach which exposed files belonging to customers. As we explained in our article about 1Password being a victim of this breach, it’s normal for Okta support to ask customers to upload a file known as an HTTP Archive (HAR) file. Having this file allows the team to troubleshoot issues by replicating what’s going on in the browser.

Graham Cluley
NOVEMBER 7, 2023
Google has added a new real-time app scanning capability to Google Play Protect in order to help it better protect against malicious apps installed from outside the official app store. Read more in my article on the Tripwire State of Security blog.

Tech Republic Security
NOVEMBER 7, 2023
Speedify VPN offers speed-centered features that may not make up for its lack of security and pricey plan. Find out how this VPN measured up in our review.

Security Affairs
NOVEMBER 7, 2023
Veeam addressed multiple vulnerabilities in its Veeam ONE IT infrastructure monitoring and analytics platform, including two critical issues. Veeam addressed four vulnerabilities (CVE-2023-38547, CVE-2023-38548, CVE-2023-38549, CVE-2023-41723) in the Veeam ONE IT infrastructure monitoring and analytics platform. The vulnerability CVE-2023-38547 (CVSS score 9.9) can be exploited by an unauthenticated attacker to gain information about the SQL server connection Veeam ONE uses to access its configu

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

The Hacker News
NOVEMBER 7, 2023
ChatGPT: Productivity tool, great for writing poems, and… a security risk?! In this article, we show how threat actors can exploit ChatGPT, but also how defenders can use it for leveling up their game. ChatGPT is the most swiftly growing consumer application to date. The extremely popular generative AI chatbot has the ability to generate human-like, coherent and contextually relevant responses.

Security Affairs
NOVEMBER 7, 2023
The iconic integrated resort Marina Bay Sands in Singapore has disclosed a data breach that impacted 665,000 customers. The Marina Bay Sands (MBS) luxury resort in Singapore has suffered a data breach that impacted 665,000 customers. Marina Bay Sands discovered the security breach on 20 October 2023, an unauthorized third party gained access to some of our customers’ loyalty programme membership data on 19 and 20 October 2023.

WIRED Threat Level
NOVEMBER 7, 2023
A complaint filed with the EU’s independent data regulator accuses YouTube of failing to get explicit user permission for its ad blocker detection system, potentially violating the ePrivacy Directive.
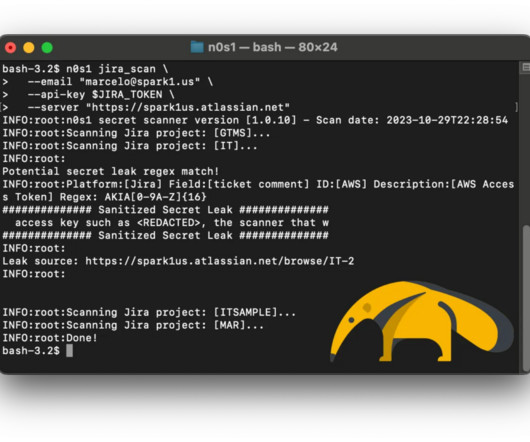
Pen Test
NOVEMBER 7, 2023
TLDR; Upgrade Confluence to a patched version and employ the open-source security scanner n0s1 to proactively address potential secret leaks. Why do I need a secret scanner? It is a widely recognized best practice for Product Security Engineers to conduct scans of the software codebase in search of potential inadvertent secret leaks. Developers may find themselves working on a new feature that requires integration with AWS and might, initially for convenience during testing, hardcode the AWS acc

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
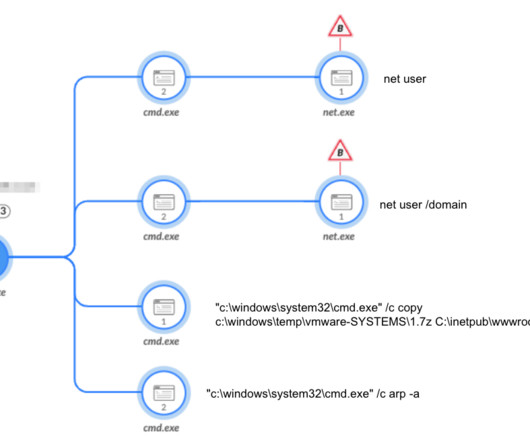
Security Affairs
NOVEMBER 7, 2023
Iran-linked Agonizing Serpens group has been targeting Israeli organizations with destructive cyber attacks since January. Iran-linked Agonizing Serpens group (aka Agrius , BlackShadow , Pink Sandstorm , DEV-0022 ) has been targeting Israeli organizations in higher education and tech sectors with destructive cyber attacks since January 2023. Palo Alto Networks’ s Unit 42 researchers reported that threat actors first attempt to steal sensitive data (i.e. personally identifiable informat
Tech Republic Security
NOVEMBER 7, 2023
VMware's Private AI platform will include interoperability with Intel, IBM's watsonx and Kyndryl.

Dark Reading
NOVEMBER 7, 2023
Active ransomware attacks against vulnerable Atlassian Confluence Data Center and Servers ratchets up risk to enterprises, now reflected in the bug's revised CVSS score of 10.

Bleeping Computer
NOVEMBER 7, 2023
Microsoft has recently removed from its store a fraudulent Ledger Live app for cryptocurrency management after multiple users lost at least $768,000 worth of cryptocurrency assets. [.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

The Hacker News
NOVEMBER 7, 2023
The North Korea-linked nation-state group called BlueNoroff has been attributed to a previously undocumented macOS malware strain dubbed ObjCShellz. Jamf Threat Labs, which disclosed details of the malware, said it's used as part of the RustBucket malware campaign, which came to light earlier this year.

Bleeping Computer
NOVEMBER 7, 2023
The Marina Bay Sands (MBS) luxury resort and casino in Singapore has disclosed a data breach that impacts personal data of 665,000 customers. [.

WIRED Threat Level
NOVEMBER 7, 2023
When a homeless man attacked a former city official, footage of the onslaught became a rallying cry. Then came another video, and another—and the story turned inside out.

Bleeping Computer
NOVEMBER 7, 2023
In a Monday advisory, Microsoft warned Outlook.com users about issues they might encounter when sending emails containing attachments. [.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

The Hacker News
NOVEMBER 7, 2023
A new variant of the GootLoader malware called GootBot has been found to facilitate lateral movement on compromised systems and evade detection.

Bleeping Computer
NOVEMBER 7, 2023
The North Korean-backed BlueNorOff threat group targets Apple customers with new macOS malware tracked as ObjCShellz that can open remote shells on compromised devices. [.

Malwarebytes
NOVEMBER 7, 2023
Since I started Malwarebytes 15 years ago the threat landscape has changed. Our offerings have evolved. And now the next chapter of our journey begins today. How did we get here? My first cyber “combatant” was an early form of adware running amok on my family’s computer. Removing it was a team effort, and it led to the creation of the first iteration of Malwarebytes, a free tool built to help everyday people find and remove malware from their computers, without needing to scour forums, write cod

SecureWorld News
NOVEMBER 7, 2023
Cyber threats pose one of the most significant risks to businesses, governments, and individuals today. As the world becomes more interconnected and data-driven, the need for cybersecurity talent has never been greater. However, a new study from ISC2 reveals that the supply of cybersecurity professionals worldwide continues to lag far behind demand.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
NOVEMBER 7, 2023
Shared service provider TransForm has published an update on the cyberattack that recently impacted operations in multiple hospitals in Ontario, Canada, clarifying that it was a ransomware attack. [.

The Hacker News
NOVEMBER 7, 2023
The Pakistan-linked threat actor known as SideCopy has been observed leveraging the recent WinRAR security vulnerability in its attacks targeting Indian government entities to deliver various remote access trojans such as AllaKore RAT, Ares RAT, and DRat.

Hack the Box
NOVEMBER 7, 2023
Wondering what it takes to become a cybersecurity engineer? Here’s a complete career guide with insights from experienced security professionals!

Penetration Testing
NOVEMBER 7, 2023
pmkidcracker This program is a tool written in Python to recover the pre-shared key of a WPA2 WiFi network without any de-authentication or requiring any clients to be on the network. It targets the... The post pmkidcracker: crack WPA2 passphrase with PMKID value without clients or de-authentication appeared first on Penetration Testing.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content