New Variant of XLoader macOS Malware Disguised as 'OfficeNote' Productivity App
The Hacker News
AUGUST 22, 2023
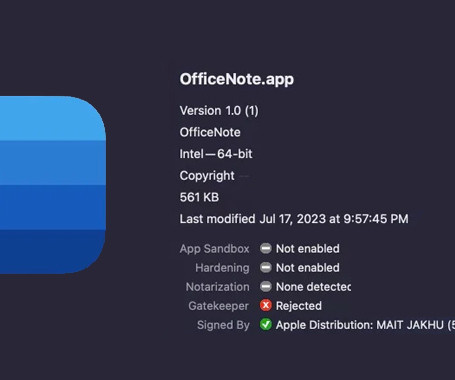
A new variant of an Apple macOS malware called XLoader has surfaced in the wild, masquerading its malicious features under the guise of an office productivity app called "OfficeNote." "The The application








































Let's personalize your content