T Mobile Retailer hacks into Company Servers
CyberSecurity Insiders
DECEMBER 18, 2022
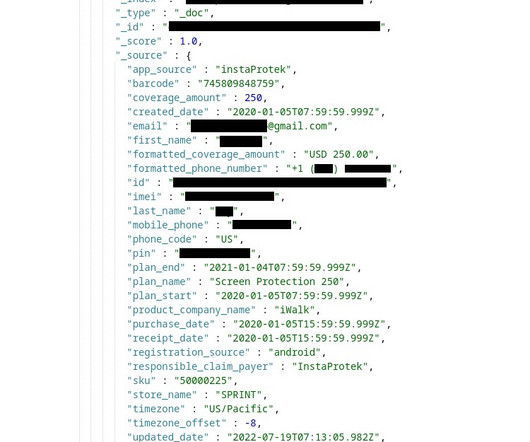
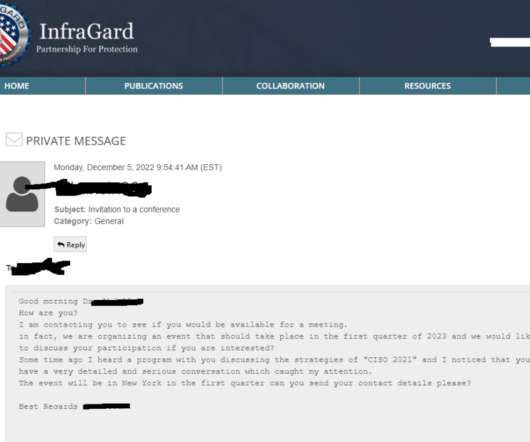
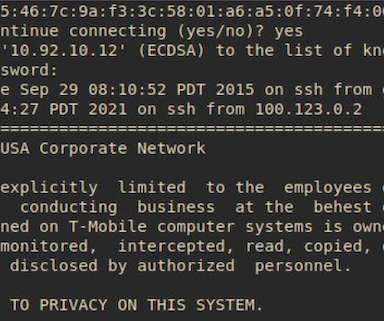
Argishti Khudaverdyan, a former retailer of T-Mobile company, received a 10-year jail imprisonment sentence at the end of last as he was found guilty of hacking into the servers of the telecom provider and gaining access to phone unlocking and unblocking of cellphones.






































Let's personalize your content