Presenting the Security Outcomes Study, Volume 2
Cisco Security
DECEMBER 7, 2021
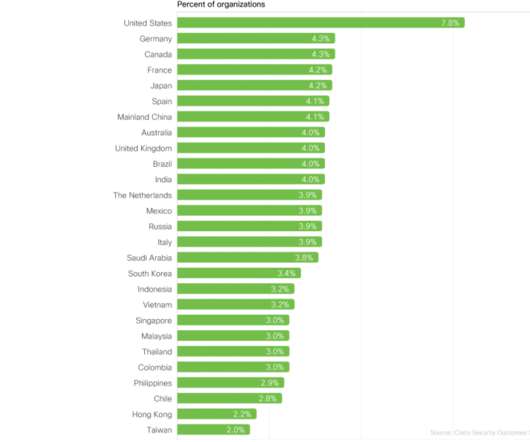
For example , Accurate Threat Detection was one of our top drivers , but what technologies, processes, and staffing models help achieve success in this arena ? What about insourcing or outsourcing threat management? . Figure 2: Effect of staffing models on perceived threat detection and incident response capabilities.














































Let's personalize your content