Where You Can Find the Industry-First Software Supply Chain Security Toolkit
Security Boulevard
MAY 16, 2022
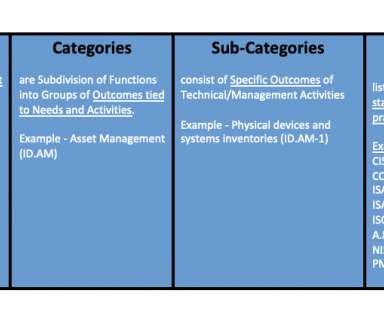
The visual, web-based resource is available to everyone and is designed to help organizations evaluate and plan the crucial steps they need to tackl e effective software supply chain security. Recommended-Resources. The Linux Foundation SLSA (Supply-chain Levels for Software Artifacts). UTM Medium. UTM Source. UTM Campaign.













































Let's personalize your content