DMARC Setup & Configuration: Step-By-Step Guide
eSecurity Planet
JUNE 1, 2023
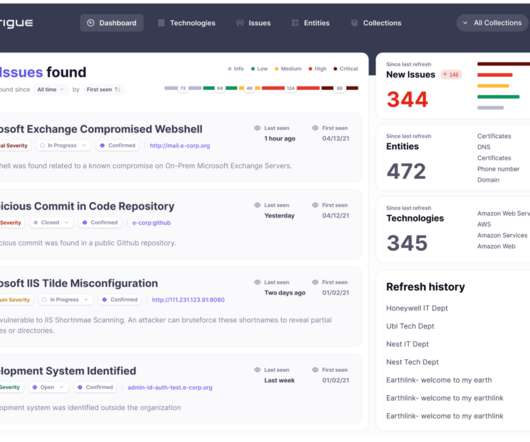
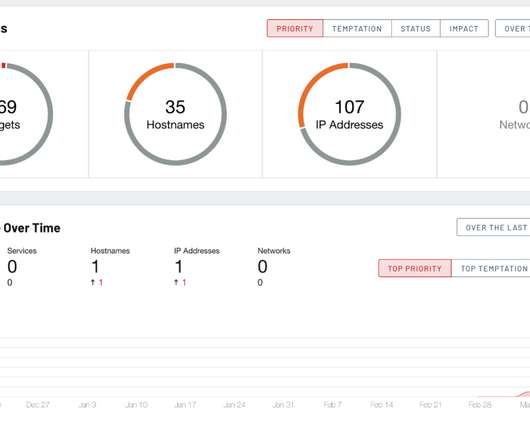
At a high level, implementation of the Domain-based Message Authentication, Reporting and Conformance (DMARC) standard can be done simply and easily for outgoing mail by adding a text file to an organization’s DNS record. To avoid issues, we need to understand the DMARC record tags in detail.












































Let's personalize your content