Massive iPhone Hack Targets Uyghurs
Schneier on Security
SEPTEMBER 3, 2019
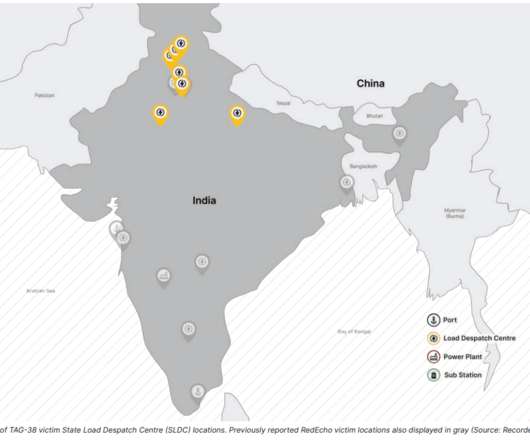
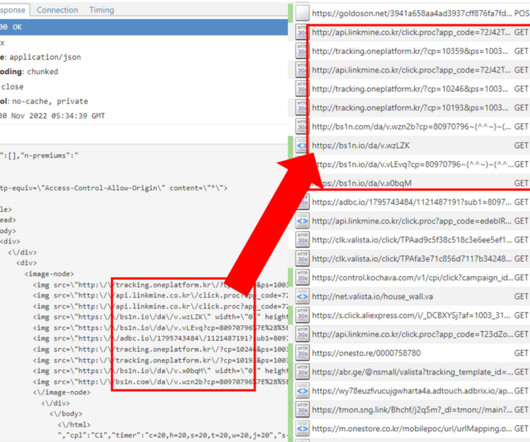
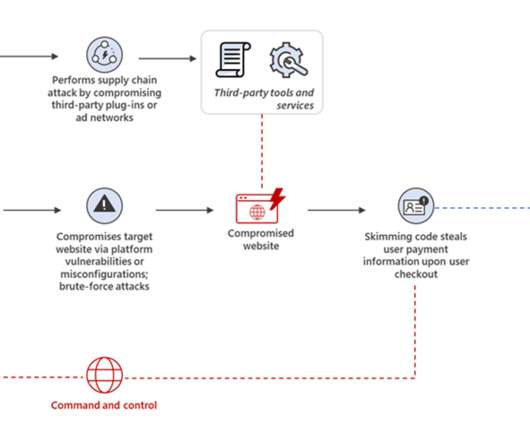
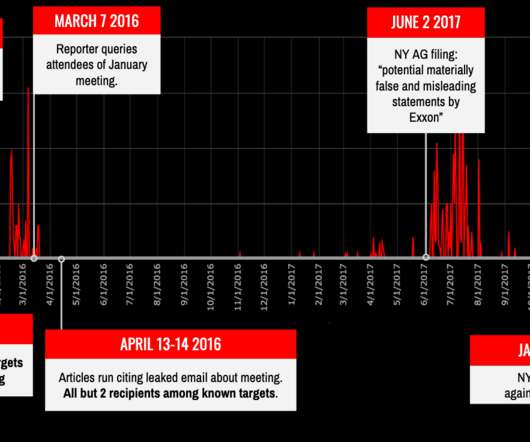
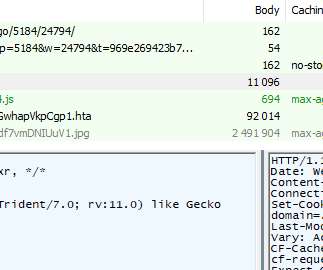
Earlier this year Google's Threat Analysis Group (TAG) discovered a small collection of hacked websites. (The Earlier this year Google's Threat Analysis Group (TAG) discovered a small collection of hacked websites. And it remained undetected for two years. (I And the politics will overshadow the tech.












































Let's personalize your content