Weekly Update 359
Troy Hunt
AUGUST 5, 2023
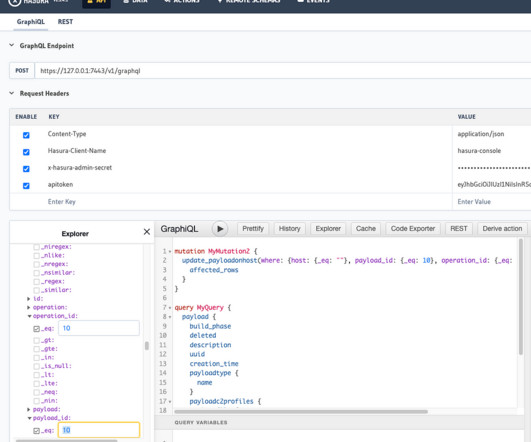
I've been speaking about it a lot in these videos over recent weeks so many of you have already know what it entails, but it's the tip of the iceberg you've seen publicly. I settled for dumping stuff in a <pre> tag for now and will invest the time in doing it right later on.)














































Let's personalize your content