SBOMs: Securing the Software Supply Chain
eSecurity Planet
OCTOBER 26, 2021
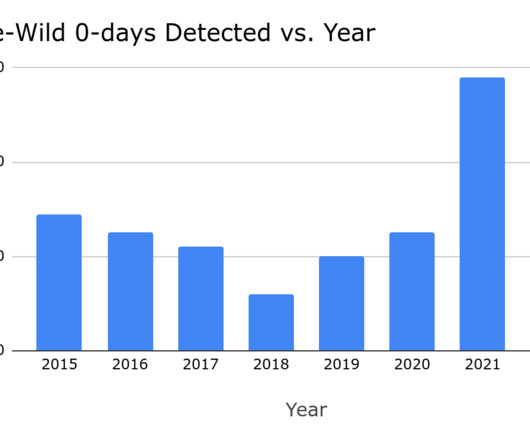
With a simple list of components that make up a software product, SBOMs enhance transparency between software buyers and sellers, provide the necessary visibility to identify vulnerabilities , and enable rapid incident response. Source: NTIA Multistakeholder Process on Software Component Transparency Framing Working Group.














































Let's personalize your content