How to Tell if Active Directory is Compromised
eSecurity Planet
SEPTEMBER 14, 2023
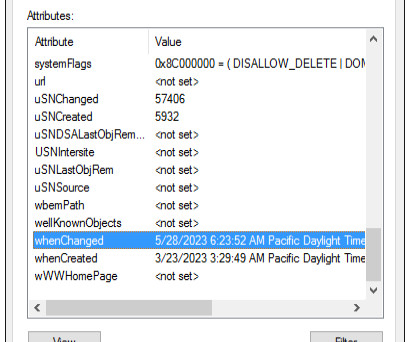
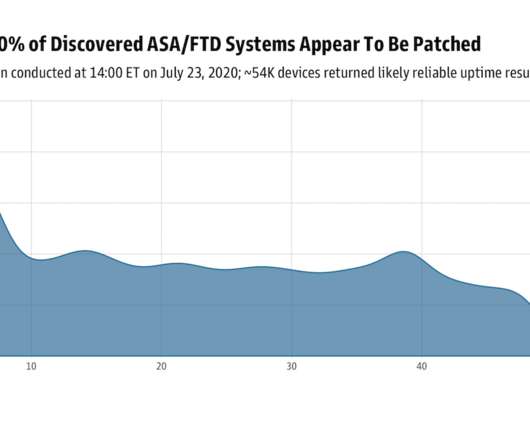
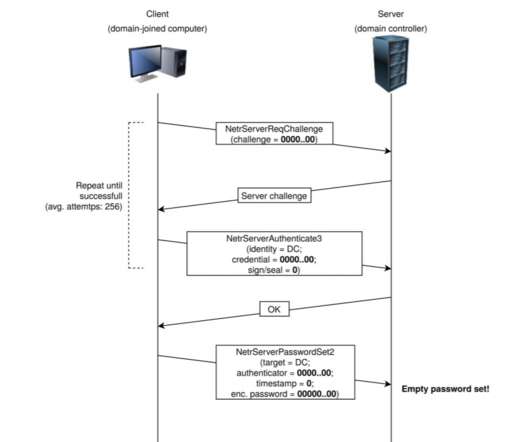
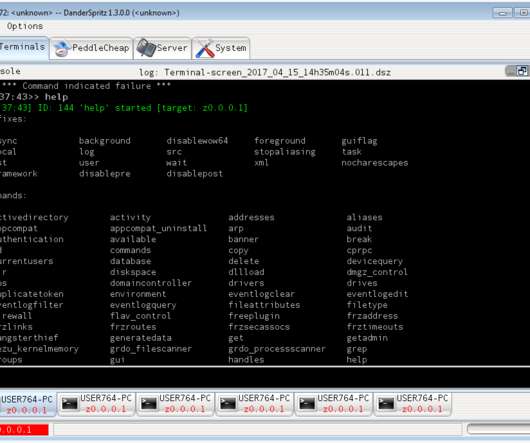
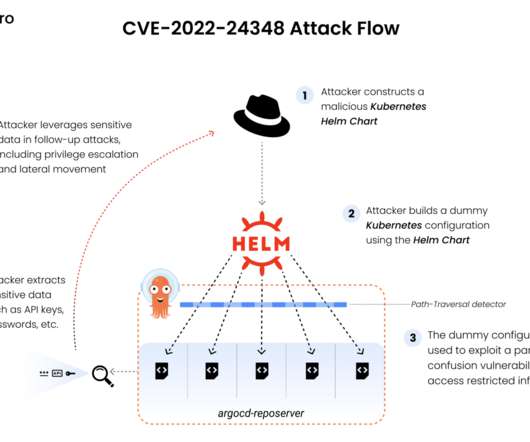
Active Directory is one of the most critically important IT assets and a frequent target of hackers, so securing it is a top priority for IT and security teams. And part of that job is checking to make sure that Active Directory hasn’t been compromised. An ordinary user won’t interact with the AdminSDHolder object.












































Let's personalize your content