NEW TECH: Breakthrough ‘homomorphic-like’ encryption protects data in-use, without penalties
The Last Watchdog
SEPTEMBER 30, 2019
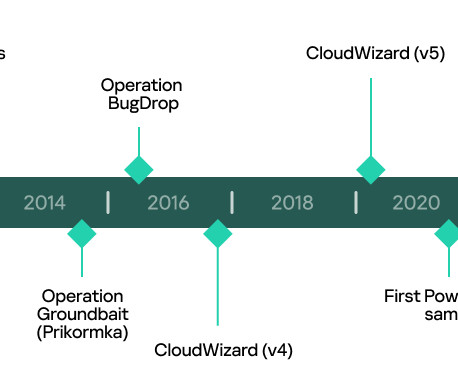
Homomorphic encryption has long been something of a Holy Grail in cryptography. Related: Post-quantum cryptography on the horizon For decades, some of our smartest mathematicians and computer scientists have struggled to derive a third way to keep data encrypted — not just the two classical ways, at rest and in transit.














































Let's personalize your content