GUEST ESSAY: Where we stand on mitigating software risks associated with fly-by-wire jetliners
The Last Watchdog
AUGUST 29, 2023
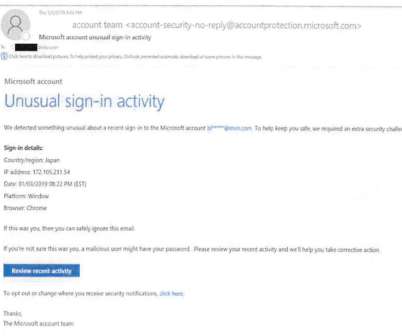
The threat of bad actors hacking into airplane systems mid-flight has become a major concern for airlines and operators worldwide. Back in 2015, a security researcher decided to make that very point when he claimed to have hacked a plane , accessed the thrust system, and made it fly higher than intended.












































Let's personalize your content