Crosspost: A Simple SOAR Adoption Maturity Model
Anton on Security
JUNE 17, 2022
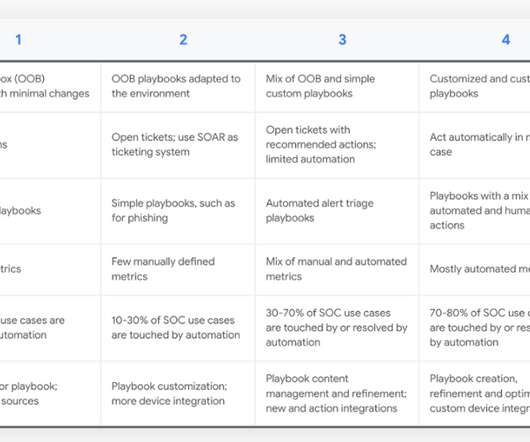
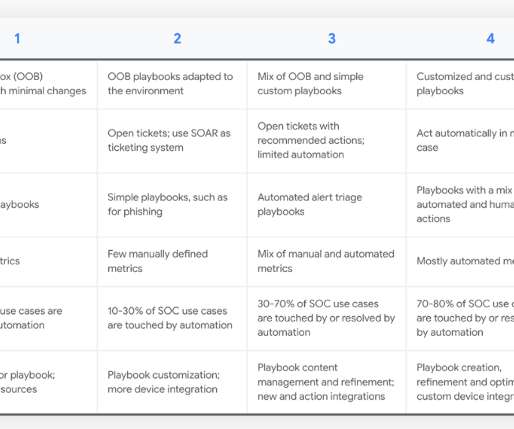
Originally written for a new Chronicle blog. For example, in my analyst days, I built a maturity model for a SOC (2018) , a SIEM deployment (2018) and vulnerability management (2017). For example, in my analyst days, I built a maturity model for a SOC (2018) , a SIEM deployment (2018) and vulnerability management (2017).








































Let's personalize your content