GhostTouch: how to remotely control touchscreens with EMI
Security Affairs
MAY 27, 2022
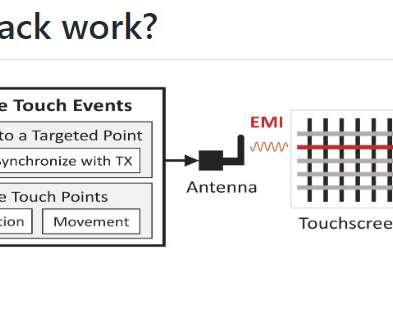
Security researchers devised a technique, dubbed GhostTouch, to remotely control touchscreens using electromagnetic signals. A team of researchers from Zhejiang University and Technical University of Darmstadt devised a technique, dubbed GhostTouch, to remotely control capacitive touchscreens using electromagnetic signals.
















Let's personalize your content