CyRC Vulnerability Analysis: Local privilege escalation vulnerability discovered
Security Boulevard
JANUARY 26, 2022
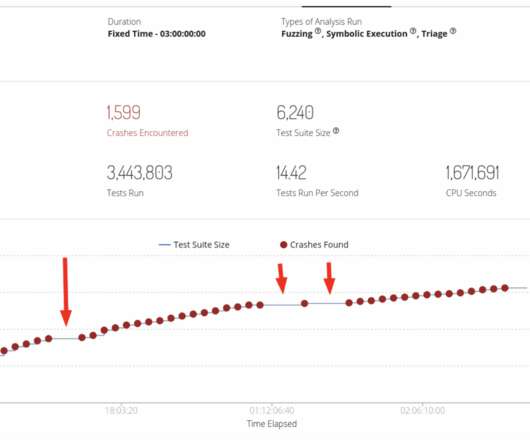
Learn more about CVE-2021-4034, a newly discovered vulnerability in PolKit software used in major Linux distributions. The post CyRC Vulnerability Analysis: Local privilege escalation vulnerability discovered appeared first on Software Integrity Blog.










































Let's personalize your content