Microsoft Data Breach Exposes Customers’ Sensitive Information
Heimadal Security
OCTOBER 20, 2022
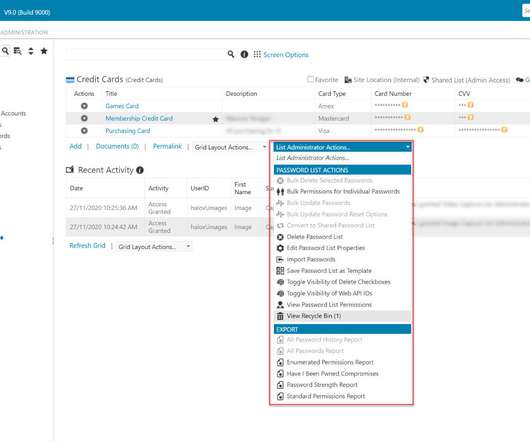
Microsoft confirms that they have been the victim of a data breach, which allowed threat actors to gain access to the personal information of some customers. The cause of the breach seems to be a misconfigured Microsoft server accessible over the Internet, security researchers claim.
























Let's personalize your content