Most Common Cyber Threats for Businesses
Heimadal Security
MARCH 25, 2022
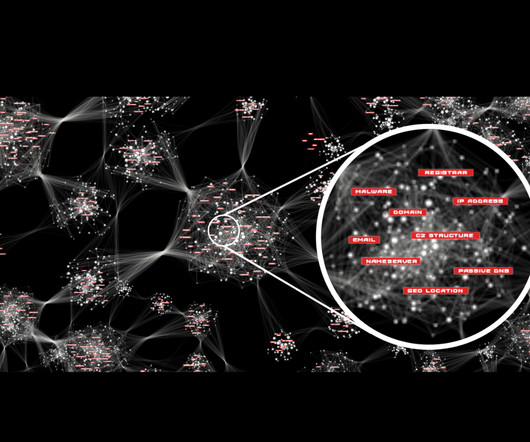
Cyber threats are a constant concern as modern-day businesses have become heavily dependent on Information and communications technology (ICT) tools to function. The post Most Common Cyber Threats for Businesses appeared first on Heimdal Security Blog.














































Let's personalize your content