Remote Desktop Threats & Remediations
Duo's Security Blog
MARCH 6, 2024
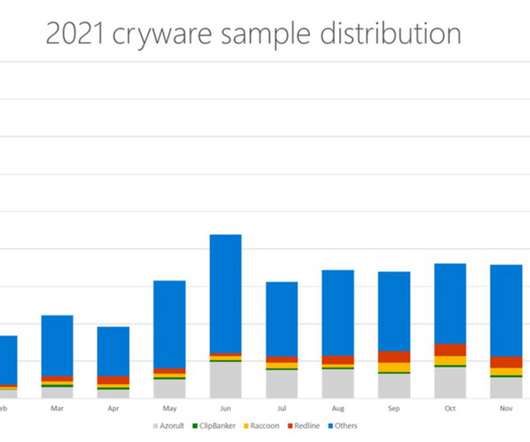
While securing RDP applications with multi-factor authentication (MFA) is an essential first step, we have seen a recent uptick in large-scale RDP attacks that can successfully subvert traditional MFA depending on the account policies and configuration. Summary Basic MFA is a necessary first step in securing RDP applications.


































Let's personalize your content