GUEST ESSAY: The privacy implications of facial recognition systems rising to the fore
The Last Watchdog
NOVEMBER 19, 2018
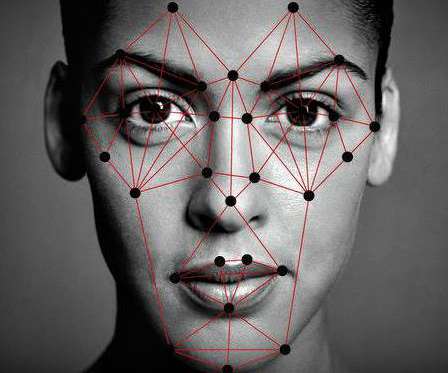
Tech advances are accelerating the use of facial recognition as a reliable and ubiquitous mass surveillance tool, privacy advocates warn. Assuming privacy concerns get addressed, much wider consumer uses are envisioned in areas such as marketing, retailing and health services. Related: Drivers behind facial recognition boom.

































Let's personalize your content