How Machine Learning Can Accelerate and Improve the Accuracy of Sensitive Data Classification
Thales Cloud Protection & Licensing
DECEMBER 11, 2023
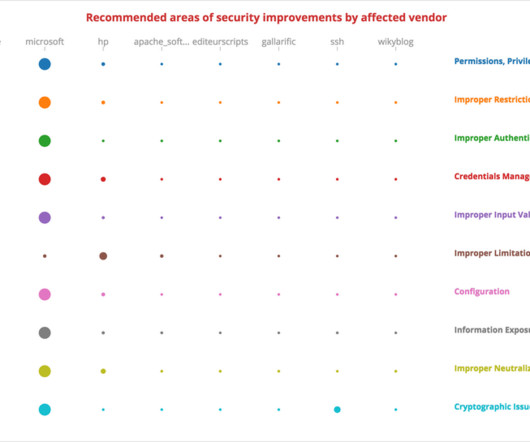
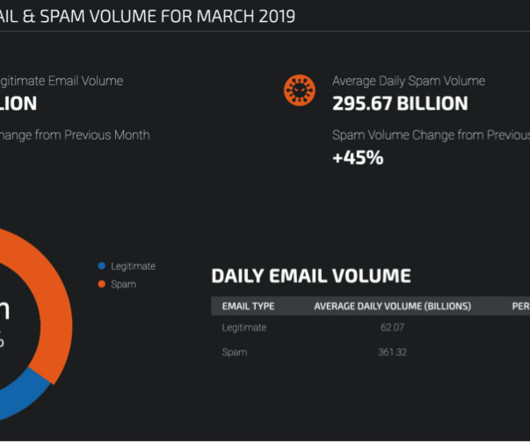
How Machine Learning Can Accelerate and Improve the Accuracy of Sensitive Data Classification madhav Tue, 12/12/2023 - 05:21 Given the pace of data growth and the complexity of hybrid IT environments, the discovery and classification of sensitive data is no simple task.






























Let's personalize your content