GUEST ESSAY: Why online supply chains remain at risk — and what companies can do about it
The Last Watchdog
JUNE 30, 2021
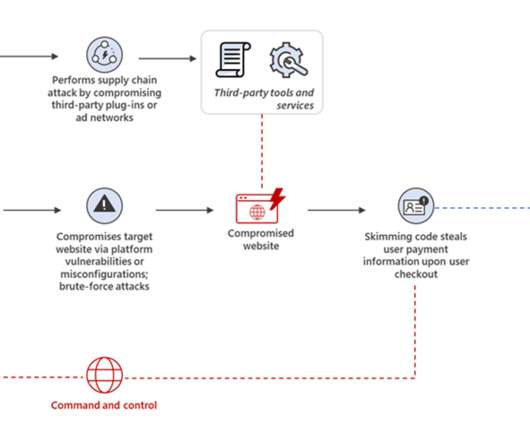
Today’s websites integrate dozens of third-party service providers, from user analytics to marketing tags, CDNs , ads, media and these third-party services load their code and content into the browser directly. are used to gain access to third party servers. Supply chain attack tactics.






































Let's personalize your content