Remote Working One Year On: What the Future Holds for Cybersecurity
Security Boulevard
MARCH 19, 2021
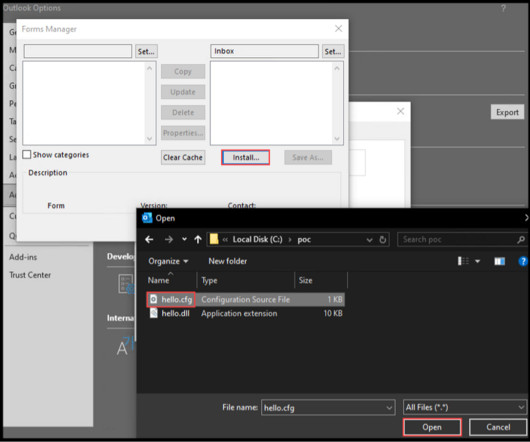
<a href='/blog?tag=Inbound tag=Inbound Threats'>Inbound Threats</a> <a href='/blog?tag=File tag=File Transfers'>File Transfers</a> <a href='/blog?tag=Email Luckier people had a home office or spare room to work from, while others had to make do with the kitchen table or the sofa.


































Let's personalize your content