The Silk Wasm: Obfuscating HTML Smuggling with Web Assembly
NetSpi Technical
FEBRUARY 26, 2024
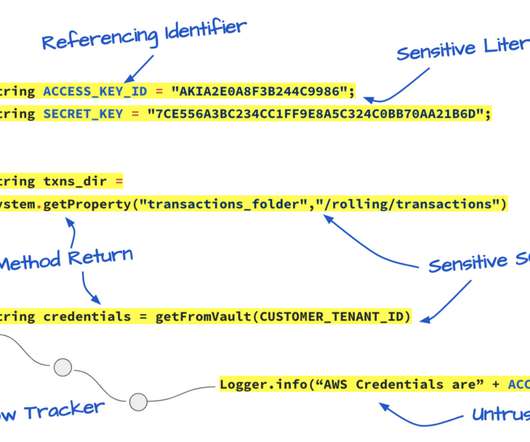
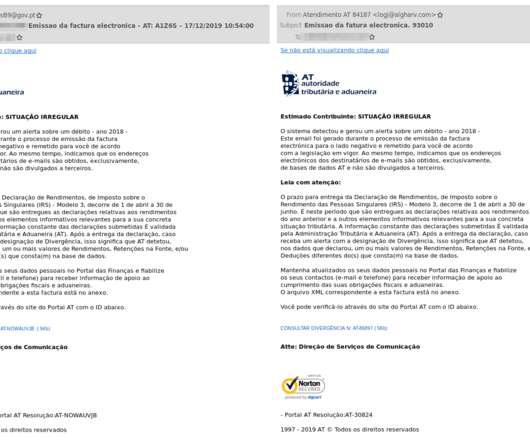
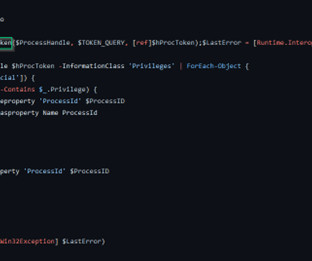
The technique does this by embedding the malicious file within the page, usually in a base64 encoded string. The technique was first demonstrated by Outflank in the following blog post. To bypass this detection, I looked for other methods of running code in the browser, that might not be quite so obvious and readable by a proxy.




























Let's personalize your content