Accurate and Reliable Threat Detection for your Security Program
Cisco Security
MARCH 19, 2021
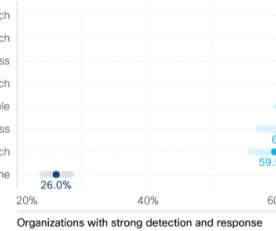
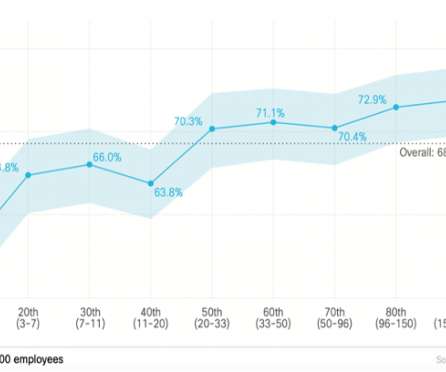
Accurate threat detection – reliability vs liability. Accurate threat detection is a difficult subject. Does the quantity of detections supersede the quality? More than one-third of the respondents were less likely to agree that their organization follows the practice of accurate threat detection.










































Let's personalize your content