5 Ways to Ensure Home Router Security with a Remote Workforce
Adam Levin
MARCH 19, 2020
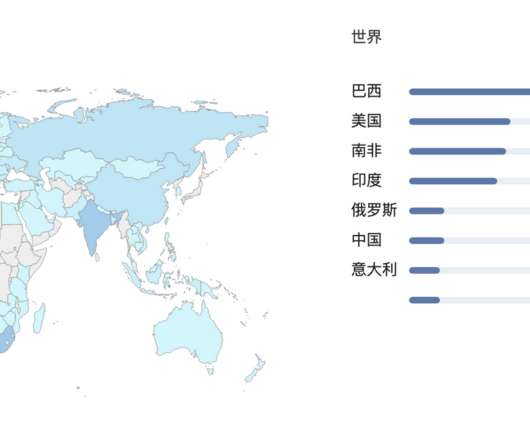
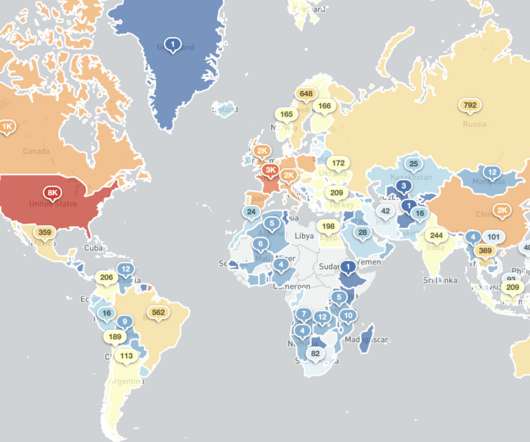
Configure a Firewall: Most routers come with a built-in firewall to block unauthorized incoming internet traffic. Encourage workers to check the existing settings and enable their router’s firewall if it isn’t running already. Passwords should be difficult to guess, but easy enough for employees to remember.

















































Let's personalize your content