New Windows/Linux Firmware Attack
Schneier on Security
DECEMBER 12, 2023
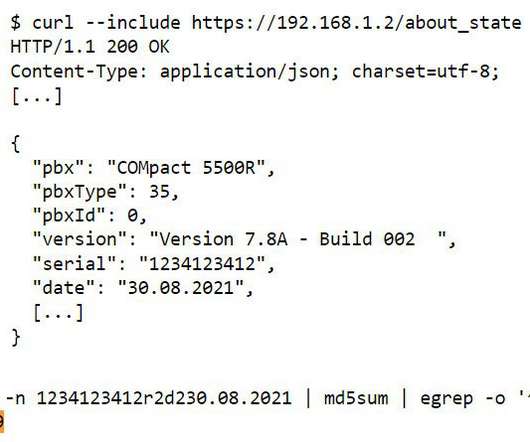
And the BIOS makers probably pulled some random graphics library off the Internet and never gave it a moment’s thought after that. So the ability has to be in the BIOS, which means that the vulnerabilities aren’t being protected by any of the OS’s defenses.












































Let's personalize your content