McAfee Data Center Security Suite: Product Overview and Analysis
eSecurity Planet
FEBRUARY 27, 2019
We review McAfee Data Center Security Suite for Databases, which offers real-time protection for databases from threats and exploits.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 products analysis-center
products analysis-center 
eSecurity Planet
FEBRUARY 27, 2019
We review McAfee Data Center Security Suite for Databases, which offers real-time protection for databases from threats and exploits.

The Last Watchdog
FEBRUARY 20, 2024
By 2026, the integration of conversational AI in contact centers will lead to a substantial $80 billion reduction in labor costs for agents. In e-commerce, it facilitates smooth product inquiries and order tracking. In customer support, it seamlessly integrates with Microsoft’s ecosystem for enhanced productivity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
JUNE 2, 2023
Overview Assura’s Security Operations Center is seeing active exploitation of a SQL Injection flaw in Progress Software’s MOVEit Transfer product first announced on May 31, 2023. The vulnerability is CVE-2023-34362.

CyberSecurity Insiders
APRIL 27, 2023
Intel gave permission to Google to hack its servers operating on its new security hardware product dubbed “Trust Domain Extensions” (TDX). On the other hand, this is not new to the web search giant, as it often involves in projects that let its engineers hack into the products developed by chipmakers for actionable insights.

Security Affairs
JUNE 3, 2022
Atlassian warned of an actively exploited critical unpatched remote code execution flaw (CVE-2022-26134) in Confluence Server and Data Center products. “Atlassian has been made aware of current active exploitation of a critical severity unauthenticated remote code execution vulnerability in Confluence Data Center and Server.

Security Affairs
APRIL 22, 2024
“I discovered how a malicious actor—without admin privileges—could hide files and processes, hide files in archives, affect prefetch file analysis, make Task Manager and Process Explorer users think a malware file was a verified executable published by Microsoft, disable Process Explorer with a denial of service (DoS) vulnerability, and more.”

The Last Watchdog
JUNE 8, 2023
Guest experts: Willy Leichter, VP of Marketing, Neal Dennis, Threat Intelligence Specialist, Cyware Leichter observes that the first-generation TIP and SOAR products fulfilled narrowly defined roles. Versions today can ingest and analyze threat feeds much more comprehensively, and, most importantly, share it strategically, he says.

Krebs on Security
APRIL 9, 2024
.” For links to individual security advisories indexed by severity, check out ZDI’s blog and the Patch Tuesday post from the SANS Internet Storm Center. Please consider backing up your data or your drive before updating, and drop a note in the comments here if you experience any issues applying these fixes.

CSO Magazine
MARCH 22, 2022
With Cato's technology, Windstream can offer a SASE solution to meet rising customer demand for a holistic network and security-as-a-service offering, says Mike Frane, VP of product management at Windstream Enterprise. To read this article in full, please click here

Krebs on Security
APRIL 20, 2021
As the largest organization dedicated to the analysis of software, Gartner’s network of analysts are well connected to the technology and software industries. ” Gartner’s 2020 “Magic Quadrant” for companies that provide “contact center as a service” offerings. .”

Security Affairs
JUNE 5, 2022
Atlassian has addressed on Friday an actively exploited critical remote code execution flaw (CVE-2022-26134) in Confluence Server and Data Center products. Atlassian has been made aware of current active exploitation of a critical severity unauthenticated remote code execution vulnerability in Confluence Data Center and Server.

CyberSecurity Insiders
OCTOBER 3, 2022
Developing intelligence to satisfy each of these stakeholders requires vast and numerous datasets, a wide range of tools, and hard to find expertise, making DIY monitoring and analysis prohibitively costly. Nisos OSINT Monitoring & Analysis. 3 – Analyst Engagement and Client Success. CUSTOMIZED INTELLIGENCE FOR YOUR NEEDS.

SC Magazine
APRIL 30, 2021
The IoT security team at the Microsoft Security Response Center said vulnerabilities discovered affect at least 25 different products made by more than a dozen organizations, including Amazon, ARM, Google Cloud, Samsung, RedHat, Apache and others. See here for a list of impacted products and patch availability.

Anton on Security
MAY 27, 2021
A SOC Tried To Detect Threats in the Cloud … Your Won’t Believe What Happened Next Now, we all agree that various cloud technologies such as SaaS SIEM help your Security Operations Center (SOC). Egress costs are there sometimes , especially if you want to move the logs from one cloud to another for analysis. Why/How?” “New

eSecurity Planet
AUGUST 14, 2023
Cybersecurity and Infrastructure Security Agency (CISA) recently published an analysis of the top 12 vulnerabilities exploited in 2022. As with other carte blanche, attackers can deploy malware at scale or perform espionage, but more dangerously, these power management consoles could be used to simply shut down the data centers entirely.
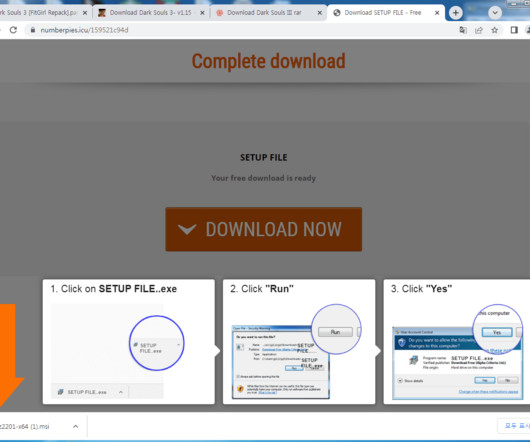
Security Affairs
FEBRUARY 27, 2023
Researchers from Ahnlab Security Emergency Response Center ( ASEC ) recently uncovered a malware campaign distributing the ChromeLoader using VHD files. ” reads the analysis published by ASEC. The analysis of the VHD files revealed multiple hidden files except for the Install.lnk file. ” continues the analysis.
Anton on Security
MAY 19, 2022
running over many regions and data centers Often immutable?—?utilizes enabled by pervasive APIs Centered on identity layer?—?mostly Pervasive encryption hampers layer 7 traffic analysis, while public APIs rewrite the rules on what a perimeter is. After all, cloud is Usually distributed?—?running

CSO Magazine
NOVEMBER 21, 2022
The analysis discovered that the threat actors behind the campaign leverage extortion without malware-based encryption, have significantly invested in call centers and infrastructure unique to attack targets, and are evolving their tactics over time. To read this article in full, please click here
Security Affairs
MARCH 18, 2022
TIM Red Team Research (RTR) researchers discovered a new flaw on Ericsson Network Manager, aka Ericsson flagship network product. TIM Red Team Research (RTR) team discovered a new vulnerability affecting Ericsson Network Manager, which is known as Ericsson flagship network product. Ericsson Network Manager and network OSS.
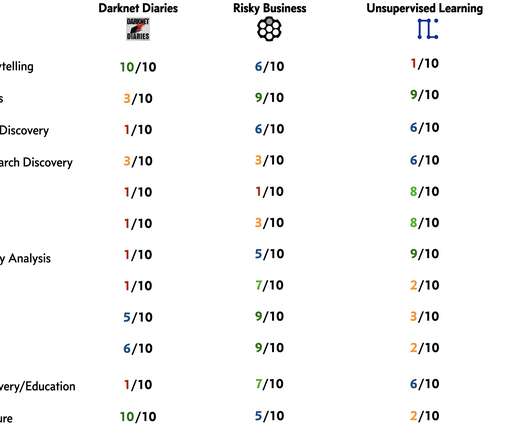
Daniel Miessler
DECEMBER 22, 2021
I did this analysis so I could capture what I cared about and how each of them provides those items in different amounts—which allows me to make better recommendations to people. Here’s my analysis and summary. But it isn’t just production quality—it’s the quality combined with the content.
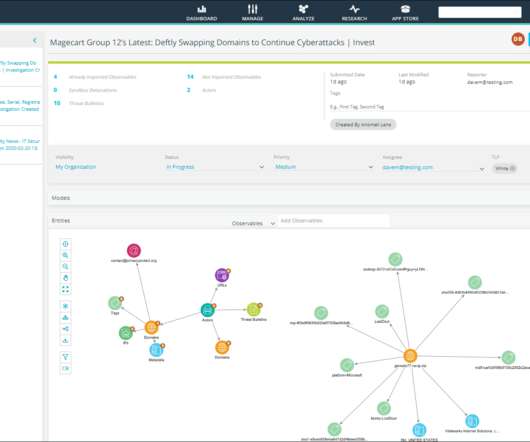
eSecurity Planet
FEBRUARY 8, 2023
This article provides more in-depth information on the product and its features. For a comparison with other TIP products, see our list of the top threat intelligence companies. It also integrates with other security products, including SIEMs, firewalls, endpoint products and more. million since launch.

Thales Cloud Protection & Licensing
JANUARY 20, 2022
Many employees work in areas where mobile phones are not allowed such as production workshops, data centers, hospitals, or labs that house medical analysis equipment. Workstations are often shared between several workers (in call centers, shop floor, retail stores.). Chitwan Arora | Product Manager at Thales.

Security Affairs
JANUARY 23, 2024
It serves as a centralized and comprehensive management platform for VMware’s virtualized data centers. Cybersecurity and Infrastructure Security Agency (CISA) added a VMware vCenter Server Out-of-Bounds Write bug, tracked as CVE-2023-34048 , to its Known Exploited Vulnerabilities (KEV) catalog. reads the report published by Mandiant.

Security Affairs
JUNE 5, 2022
Proof-of-concept exploits for the critical CVE-2022-26134 vulnerability in Atlassian Confluence and Data Center servers are available online. Proof-of-concept exploits for the critical CVE-2022-26134 flaw, affecting Atlassian Confluence and Data Center servers, have been released. reads the analysis published by Volexity.

Krebs on Security
FEBRUARY 8, 2021
The Ukrainian attorney general’s office said it worked with the nation’s police force to identify a 39-year-old man from the Ternopil region who developed a phishing package and special administrative panel for the product. The security flaw was briefly alluded to in a 2018 writeup on U-Admin by the SANS Internet Storm Center.

Cisco Security
JUNE 9, 2022
Forrester Consulting recently conducted an independent analysis of organizations using Secure Firewall. The study showed that customers realized a 195% in total ROI when managing their firewall fleet through Cisco Secure Firewall Management Center (FMC). Director Product Management, Cisco Secure. We are not done.

Security Affairs
SEPTEMBER 3, 2023
ransomware builder used by multiple threat actors Cisco fixes 3 high-severity DoS flaws in NX-OS and FXOS software Cybercrime Unpacking the MOVEit Breach: Statistics and Analysis Cl0p Ups The Ante With Massive MOVEit Transfer Supply-Chain Exploit FBI, Partners Dismantle Qakbot Infrastructure in Multinational Cyber Takedown U.S.

SecureList
NOVEMBER 20, 2023
Furthermore, we conducted an analysis of Black Friday–related spam and phishing activity in the weeks leading up to Black Friday. Phishing Since the beginning of fall, Kaspersky products have consistently identified a substantial number of scam stores offering clothing, appliances, and gadgets.

Lenny Zeltser
SEPTEMBER 26, 2019
What malware analysis approaches work well? 7:17) What role do automated sandboxes play in the analysis process? (14:30) 14:30) What are your go-to tools for code-level analysis? (20:15) 20:15) Which malware analysis tools are useful for people who are just getting started with this type of work? (27:21)

Cisco Security
MAY 11, 2021
These document guides help customers and partners triage Cisco products that are suspected of being compromised. Assessing the Integrity of Cisco Firepower Management Center. Cisco is pleased to announce two new document additions to the Firepower Forensic Investigation Procedures for First Responders. We’d love to hear what you think.

SC Magazine
MARCH 22, 2021
Applications are moving from the data center to the cloud, more employees are working remotely than ever before, and users access data by a wide variety of company and personally-owned devices. Here are four basic principles of SASE security pros need to understand: Data centers are no longer the concentration point of the network.

Security Affairs
JUNE 5, 2021
The ATT&CK knowledge base is used by cyber threat analysts for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. ” reads one of the studies. . ” reads one of the studies. ” states the guide.
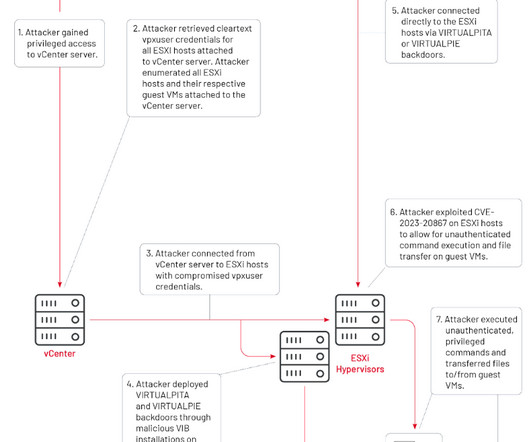
Security Affairs
JANUARY 19, 2024
It serves as a centralized and comprehensive management platform for VMware’s virtualized data centers. Mandiant researchers reported that China-linked APT group UNC3886 has been exploiting vCenter Server zero-day vulnerability CVE-2023-34048 since at least late 2021. ” reads the advisory.

CyberSecurity Insiders
MAY 30, 2023
Terminology AWS Region – a physical location around the world where we cluster data centers. AWS Availability Zone (AZ) – is one or more discrete data centers with redundant power, networking, and connectivity in an AWS Region. This can include uncounted third parties as well.

CyberSecurity Insiders
OCTOBER 26, 2021
The scope of cybersecurity is quite broad, but I’d like to share some of our Stories from the SOC experiences, to show how we provide services and products to protect our customers in real-life scenarios. In our analysis of what turned out to be the activity of the Sodinokibi ransomware gang, we were able to move quickly.

McAfee
AUGUST 4, 2021
Miercom has been reviewing network products for over 30 years, forming standardized test programs that have grown into a worldwide evaluation service for the latest technology. About the Testing.

Cisco Security
MAY 14, 2021
At the publishing of the previous Q3 2019 Forrester Wave report for Endpoint Security Suites, Secure Endpoint was lauded as one of the least obtrusive security products to end-user productivity. Broad OS Support – for both client and servers of Windows, Mac OS, and Linux.

Anton on Security
FEBRUARY 5, 2024
If you are like us, you may be surprised that, in 2024, traditional security information and event management (SIEM) systems are still the backbone of most security operations centers (SOC). here we sound like marketing people, but it is also true; old product with a chat bot is still an old product]. are we a bit harsh here?

SC Magazine
JULY 1, 2021
This has created what the Center for internet Security calls the “fog of more,” where a deluge of choices make decisions difficult to manage. Before retiring in 2012 Sager oversaw all NSA red and blue teams, as well as all security product evaluation teams. So how should one choose?

SecureWorld News
MAY 15, 2022
ISO/SAE 21434 specifies the practices that safeguard against design, development, production, operation, maintenance, and decommissioning risks in the electrical and electronic systems of road vehicles. ISO/SAE 21434 is a product of Technical Committee 2, Subcommittee 32. A look at the future.

eSecurity Planet
APRIL 12, 2024
Consider these factors: Sensitive data handling: Determine whether your company handles customers’ personally identifiable information (PII), proprietary software code, product designs, or any other unique creations crucial for your company’s competitive edge. Conduct content analysis to improve safety measures.
Thales Cloud Protection & Licensing
NOVEMBER 11, 2021
The volume of confidential documents created daily is, frankly, incalculable, and the volume of “everything” distributed across multiple data centers around the world is much, much more. Nisha Amthul | Senior Product Marketing Manager. Don't Encrypt Everything; Protect Intelligently. Thu, 11/11/2021 - 09:30. More About This Author >.

SC Magazine
MARCH 2, 2021
Visa has been a leader in establishing a risk operations center. Today’s columnist, Padraic O’Reilly of CyberSaint, explains why more companies find the need for a ROC to complement its security operations center. We see a new, dedicated function arising, the risk operations center (ROC). Why companies need a ROC.
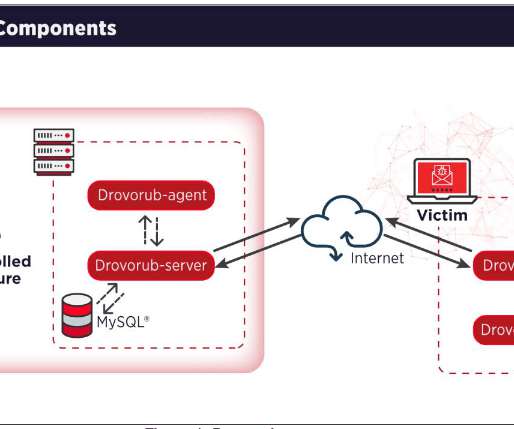
Security Affairs
AUGUST 13, 2020
The group operates out of military unity 26165 of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS). The group was involved also in the string of attacks that targeted 2016 Presidential election. Most of APT28s’ campaigns leveraged spear-phishing and malware-based attacks.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content