6 Common Phishing Attacks and How to Protect Against Them
The State of Security
OCTOBER 13, 2021
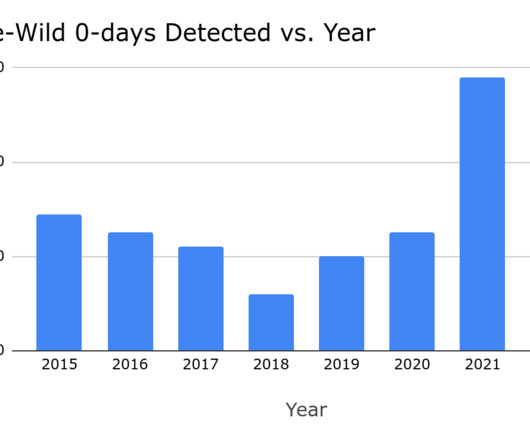
Phishing attacks continue to play a dominant role in the digital threat landscape. In its 2021 Data Breach Investigations Report (DBIR), Verizon Enterprise found phishing to be one of the most prevalent action varieties for the data breaches it analyzed. That’s up […]… Read More. That’s up […]… Read More.









































Let's personalize your content