Google TAG spotted actors using new code signing tricks to evade detection
Security Affairs
SEPTEMBER 26, 2021
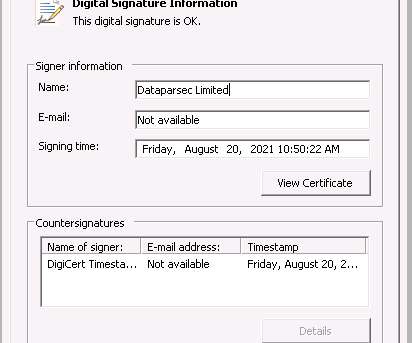
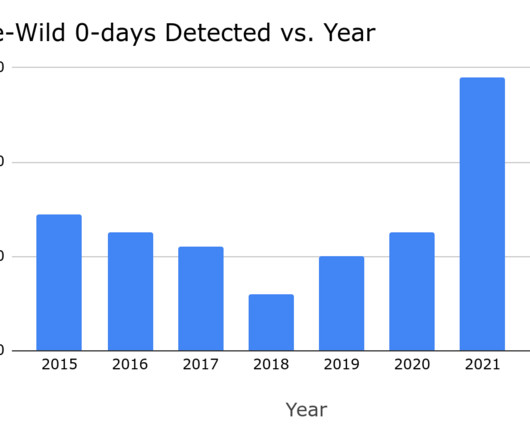
Researchers from Google’s TAG team reported that financially motivated actors are using new code signing tricks to evade detection. Researchers from Google’s Threat Analysis Group reported that financially motivated actors are using new code signing tricks to evade detection. ” read the analysis published by Google TAG.





































Let's personalize your content