Thieves Using AirTags to “Follow” Cars
Schneier on Security
DECEMBER 6, 2021
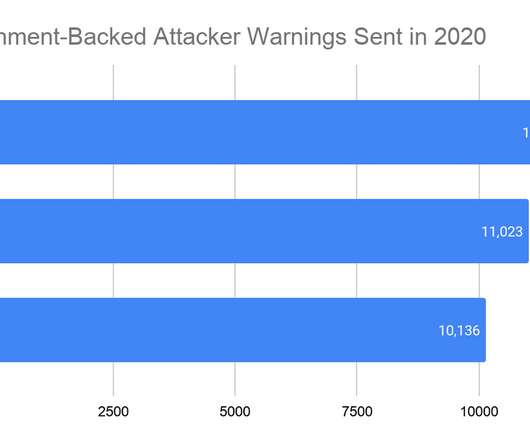
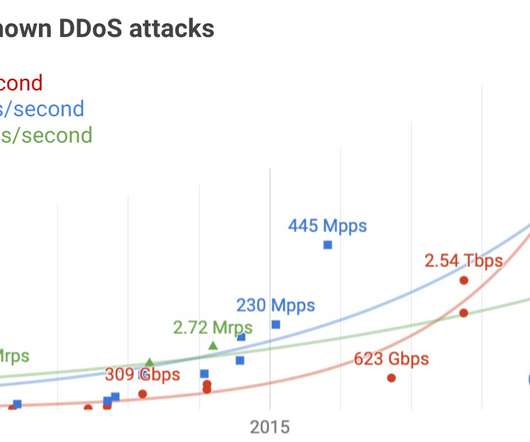
Brand name “air tags” are placed in out-of-sight areas of the target vehicles when they are parked in public places like malls or parking lots. Apple responded with a slew of anti-stalking measures , but those are more intended for keeping people safe than cars.








































Let's personalize your content