Previously undocumented Aoqin Dragon APT targets entities in Southeast Asia and Australia
Security Affairs
JUNE 9, 2022
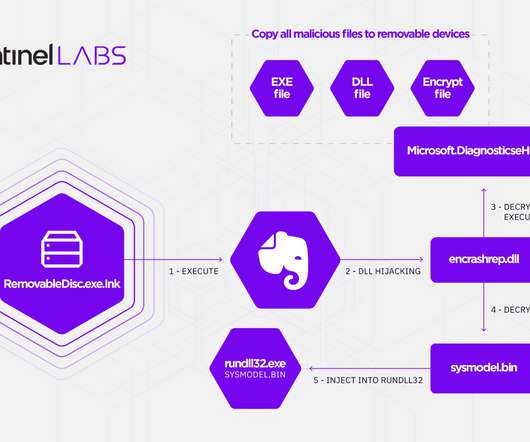
The group has been active since at least 2013, the Aoqin Dragon was observed seeking initial access primarily through document exploits and the use of fake removable devices. Luring users into double-clicking a fake Anti-Virus to execute malware in the victim’s host. The loader will check the file path first and decrypt the payloads.













































Let's personalize your content