Top 3 Data Visualization Capabilities in a CASB Solution
McAfee
APRIL 2, 2020
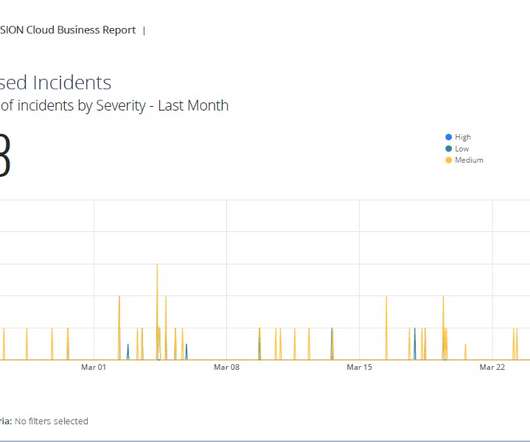
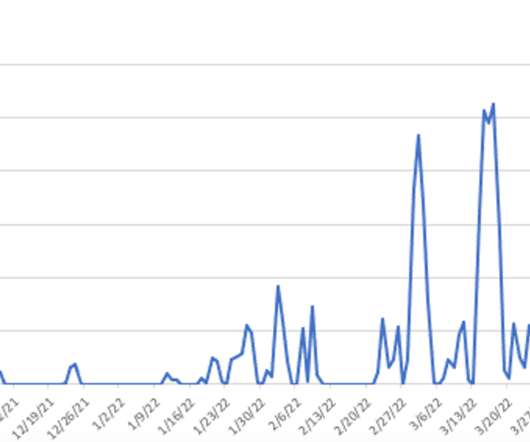
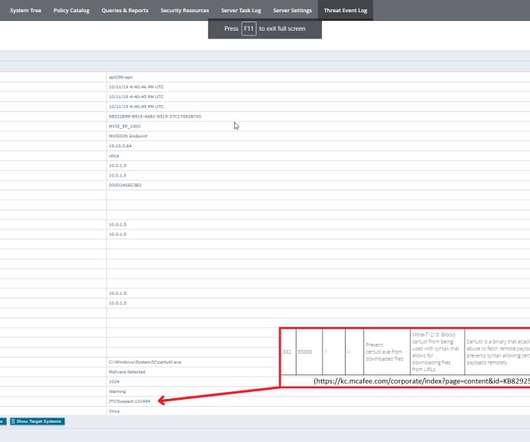
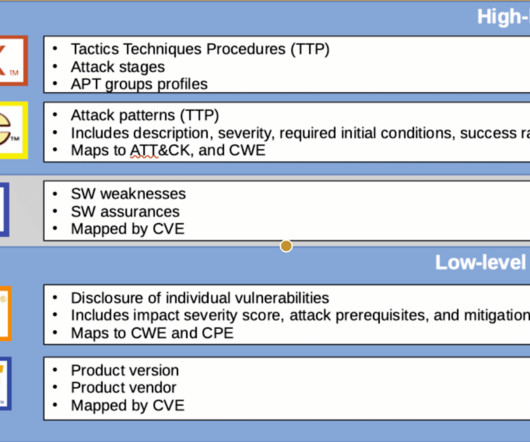
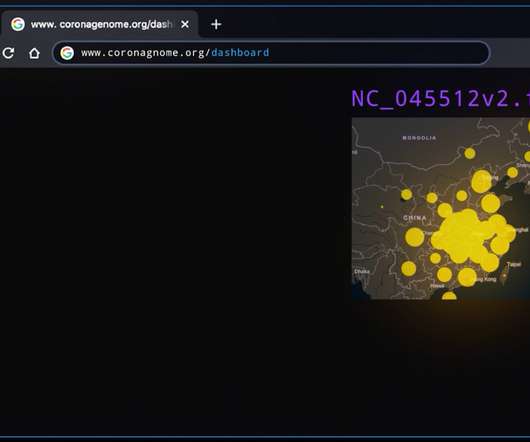
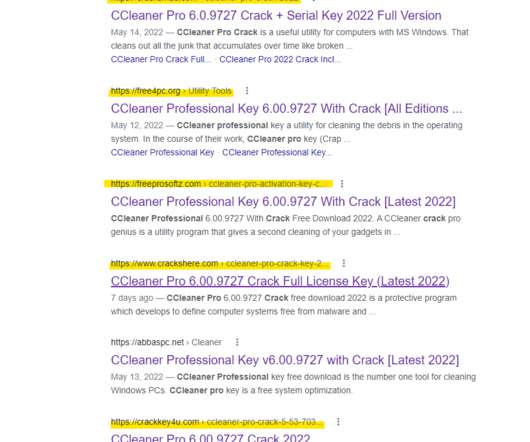
The visualization capabilities of a CASB solution play a key role in better understanding the company’s cloud security posture. MVISION Cloud customers have given feedback that data visualization within a CASB is critical to support their operations. Visualization of services and risk using multiple dimensions.








































Let's personalize your content