Source Code Leak – What We Learned and How You Can Protect Your IP
McAfee
JULY 31, 2020
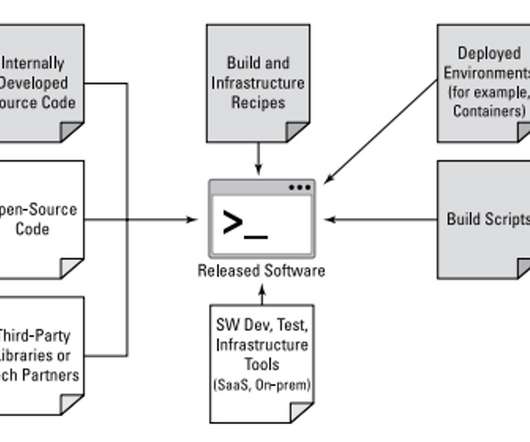
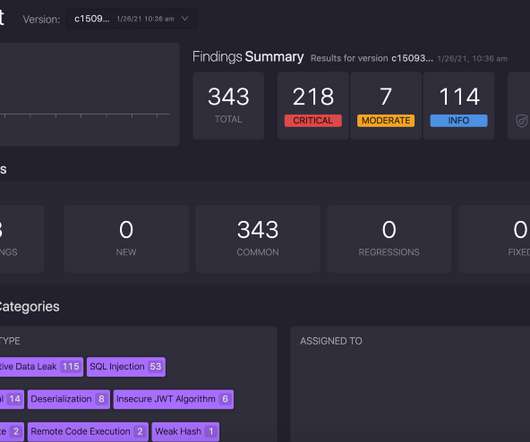
This week we learned about a leak of source code from 50 prominent companies , posted by a Swiss IT consultant. These come after another recent leak of source code from Nintendo, prompting us to comment on the issue of IP protection and secure development pipelines. . How You Can Protect Your IP .













































Let's personalize your content