Guest Blog: TalkingTrust. What’s driving the security of IoT?
Thales Cloud Protection & Licensing
MARCH 10, 2021
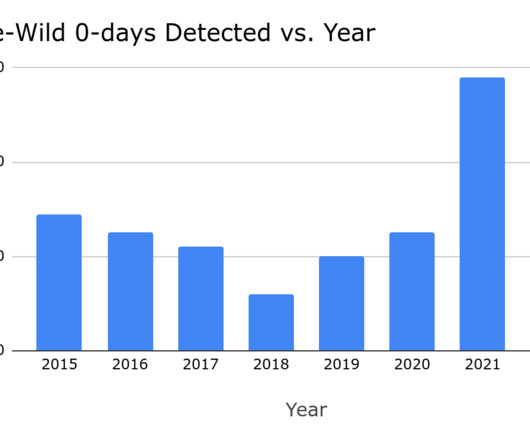
Guest Blog: TalkingTrust. Connectivity enables powerful, revenue-generating capabilities…from data telemetry and runtime analytics, to effectively predicting and maintenance requirements. The problem becomes – how do we make sure we’re securing these “driving data centers” against the risks and threats that lurk on the Internet?










































Let's personalize your content