New Phishing Method Discovered
Heimadal Security
FEBRUARY 23, 2022
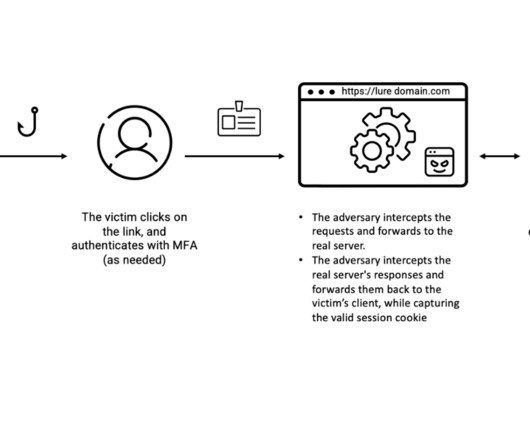
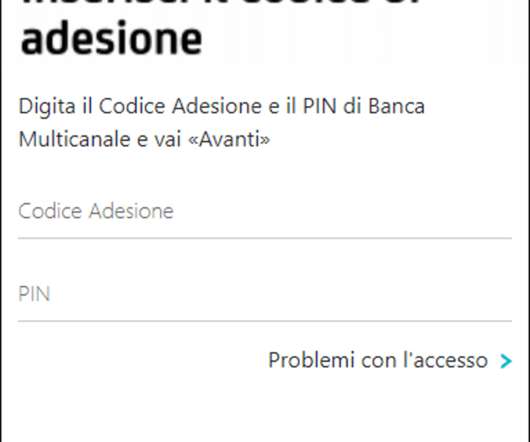
Phishing is a harmful tactic employed by cyber attackers in order to obtain sensitive information (such as credit card numbers, usernames, and passwords). The information collected via phishing may be utilized for a […]. The information collected via phishing may be utilized for a […].








































Let's personalize your content