Stealing More SRE Ideas for Your SOC
Anton on Security
DECEMBER 21, 2021
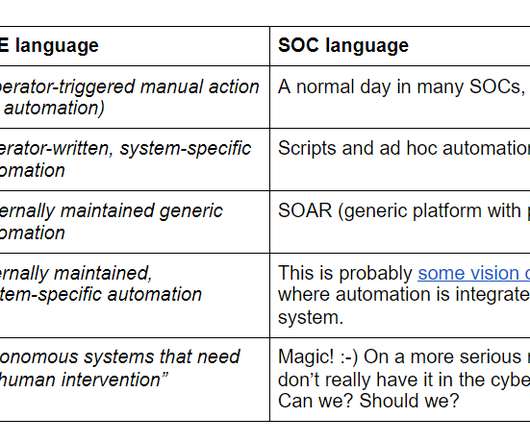
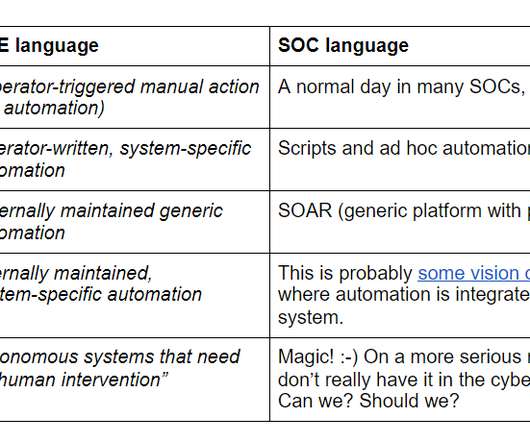
As we discussed in “Achieving Autonomic Security Operations: Reducing toil” (or it’s early version “Kill SOC Toil, Do SOC Eng” ), your Security Operations Center (SOC) can learn a lot from what IT operations learned during the SRE revolution. However, both security operations center practitioners and SREs agree?—?consistency















































Let's personalize your content