CVE-2024-21378 — Remote Code Execution in Microsoft Outlook
NetSpi Technical
MARCH 11, 2024
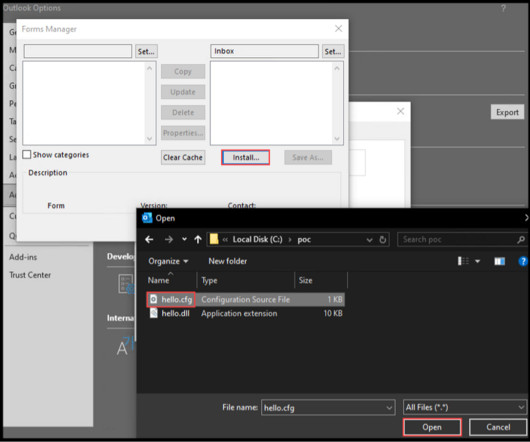
This blog will cover how we discovered CVE-2024-21378 and weaponized it by modifying Ruler , an Outlook penetration testing tool published by SensePost. In late 2015, Nick Landers, Co-Founder of Dreadnode, published a blog on the abuse of Outlook Rules for RCE. However, the syncing capability of these form objects was never altered.














































Let's personalize your content